Core Capabilities
Core Modules
Protection Services
Offensive Security
Application Security
Infrastructure Security
Full-scope adversary simulation that tests your people, processes, and technology. We don't just find vulnerabilities — we prove exploitability through realistic attack chains.
Real threat actor TTPs
Human factor testing
Facility breach testing
Full attack chains
// CLASSIFIED: Adversary simulation request
// All communications encrypted
Securing critical infrastructure for forward-thinking organizations.




While both identify vulnerabilities, red teaming provides a comprehensive assessment of your organization's detection and response capabilities.
Vulnerability-focused assessment
Full adversary simulation
Our red team operators simulate the tactics, techniques, and procedures used by real threat actors targeting your industry.
Test physical security controls including access badges, tailgating, and secure area penetration.
Advanced phishing, vishing, and pretexting campaigns targeting employees at all levels.
Gain initial access and move laterally through your network to reach critical assets.
Target cloud infrastructure, SaaS applications, and identity providers.
Simulate malicious insider scenarios to test detection and data loss prevention.
Test your defenses against realistic ransomware attack chains without actual encryption.
Our red team operations go beyond standard penetration testing. We simulate real-world adversary tactics, techniques, and procedures (TTPs) to test your entire security posture.
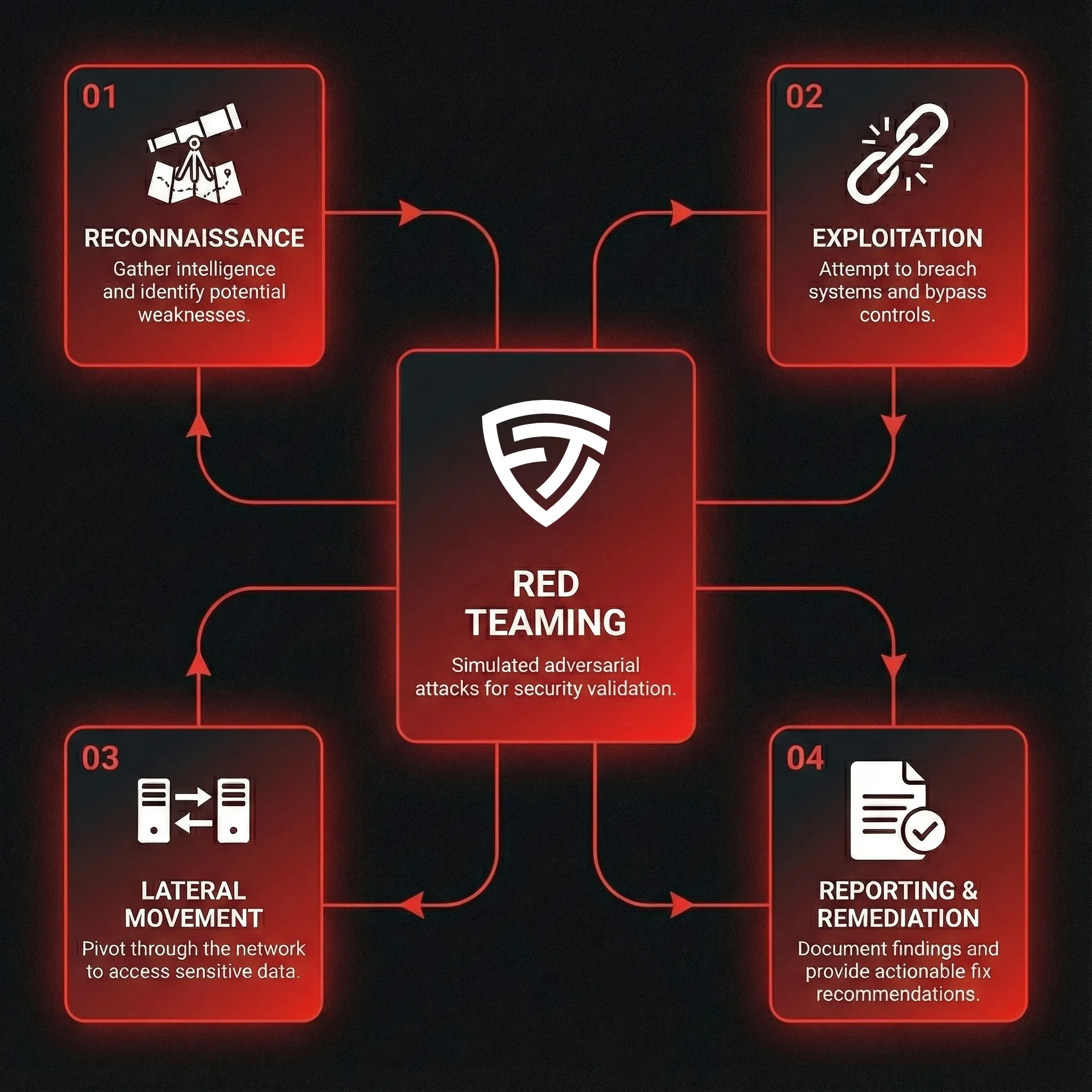
Our red team follows the same methodologies used by advanced persistent threats, mapped to MITRE ATT&CK framework.
Gather intelligence on targets, infrastructure, and personnel through OSINT and active reconnaissance.
Gain foothold through phishing, exploitation, or physical access to internal systems.
Establish persistent access and escalate privileges to maintain control.
Move through the network to reach high-value targets and critical systems.
Achieve defined objectives: data access, domain admin, or business impact demonstration.